ImaginaryCTF 2024

imaginaryCTF 2024
FORENSICS:
bom
Description: 楣瑦筴栴瑟楳渷彣桩渳獥
Attachments:chal.txt
Solution:
Inside the file, only the text þÿ is not part of the flag; the rest of the content, ictf{th4t_isn7_chin3se}, is the flag.
Flag: ictf{th4t_isn7_chin3se}
packed
Description: Packet Tracer is a cross-platform visual simulation tool designed by Cisco Systems that allows users to create network topologies and imitate modern computer networks. The software allows users to simulate the configuration of Cisco routers and switches using a simulated command line interface. (same attachment as routed)
Attachments:routed.pkg
Solution:
extrat .pkg file by ezyzip.com and get secret.png
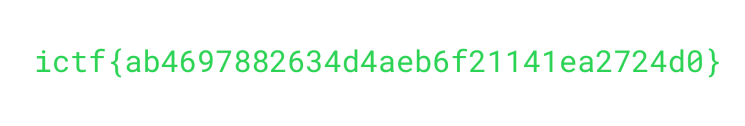
flag: ictf{ab4697882634d4aeb6f21141ea2724d0}
cartesian-1
Description: THIS IS AN OSINT CHALLENGE.
Greetings. You have been tasked with investigating the whereabouts of a potential recruit. To perform this top-secret background check, we must gather as much information as possible.
Please investigate Terrence Descartes. We know that his social accounts are relatively new, so please do not attack anything out of scope. For the sake of this series of challenges, nothing pertaining to Terry has existed before July 17, 2024. Do not investigate anything posted online before then.
Attachments: None,
search his profile on instagram
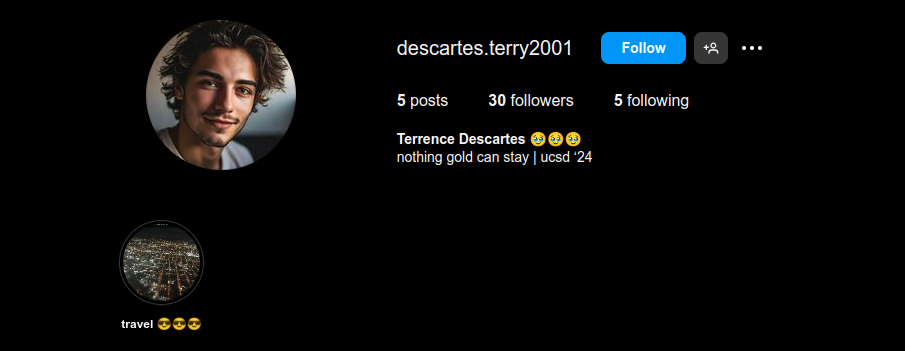
Solution:
inside his instagram story : travel 😎😎😎
flag: ictf{i_love_revealing_info_on_the_internet}
dog-mom
Description: This is an OSINT challenge.
i’m a dog mom i 🩷 dogs
Find where this picture was taken; submit your flag as ictf, both rounded to three decimal places. (example: ictf{-12.345_66.533})
Attachments:image.png

Solution: The first step is using Google Image Search and I found a clue on Flickr. However, the view through the windows is not from the Cathedral of Learning’s 36th floor because the coordinates do not match. I think it might be a different building at the same location.
location is Cathedral of Learning Panther fountain 😂
Latitude: 40.44397
Longitude: -79.95358
Flag: ictf{40.444_-79.954}
REVERSING
unoriginal
Description: i like elf reversing
Attachments: unoriginal
Solution:
Open the terminal by pressing Ctrl+Alt+T, then type the following command to check information about the ELF file.
$ file unoriginal
unoriginal: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV),
dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2,
BuildID[sha1]=e62dc74b0e909a63a0fc240a62ee75ab47936823,
for GNU/Linux 3.2.0, not stripped
next is check strings by typing following command
$ strings unoriginal
Enter your flag here:
lfqc~opvqZdkjqm`wZcidbZfm`fn`wZd6130a0`0``761gdx
Correct!
Incorrect.
or use xxd hex editor
xor 5 to get flag
a = 'lfqc~opvqZdkjqm`wZcidbZfm`fn`wZd6130a0`0``761gdx'
for i in a:
print(chr(ord(i) ^ 5), end='')
Flag: ictf{just_another_flag_checker_a3465d5e5ee234ba}
CRYPTO
base64
Description: yet another base64 decoding challenge
Attachments: Main.py out.txt sbg.png
Solution:
from Crypto.Util.number import long_to_bytes # type: ignore
secret_key = [10, 52, 23, 14, 52, 16, 3, 14, 37, 37, 3, 25, 50, 32, 19, 14, 48, 32, 35, 13, 54, 12, 35, 12, 31, 29, 7, 29, 38, 61, 37, 27, 47, 5, 51, 28, 50, 13, 35, 29, 46, 1, 51, 24, 31, 21, 54, 28, 52, 8, 54, 30, 38, 17, 55, 24, 41, 1]
out = 0
for num in secret_key[::-1]:
out *= 64
out += num
print(long_to_bytes(out).decode())
Flag: ictf{b4se_c0nv3rs1on_ftw_236680982d9e8449}
WEB
readme
Description: Try to read the flag.txt file.
Attachments: readme.tar.gz
Solution: extract the readme file by typing following command
$ tar -zxvf readme.tar.gz
then found flag inside dockerfile.
Flag : ictf{path_normalization_to_the_rescue}
MISC
sanity-check
Description: Welcome to ImaginaryCTF 2024!
Attachments: ictf{this_isnt_real}
discord
Description: Join our Discord community for updates and support! If you would like to do some more CTF after this competition, we do host daily CTF challenges on our Discord server as well. Join at https://discord.gg/ctf . You can find the flag for this challenge in the #imaginaryctf-2024 channel.
Attachments: None
Flag: ictf{fake_flag_for_testing}