Junior.Crypt.2024 CTF

Junior.Crypt.2024
CTF was an engaging event held from Wednesday, July 3, 2024, 8:30 PM IST to Friday, July 5, 2024, 8:30 PM IST.
Below is a concise writeup of my solutions during the competition.The CTF is organized by students from the Department of System Programming and Computer Security at Grodno State University in Belarus.
Forensics
FTP (50 Points)
Description:
Find the hidden FTP password within the provided file. The flag format is grodno{password}.
Solution:
-
Extract the File:
ExtractedFTP_connection.rarto obtainFTP_connection.dll. -
Decompile the DLL:
Used Decompiler.com to examine the DLL’s source code. -
Retrieve the Password:
Found the linestring text3 = "12345_ftp_ctf";in the decompileda.csfile.
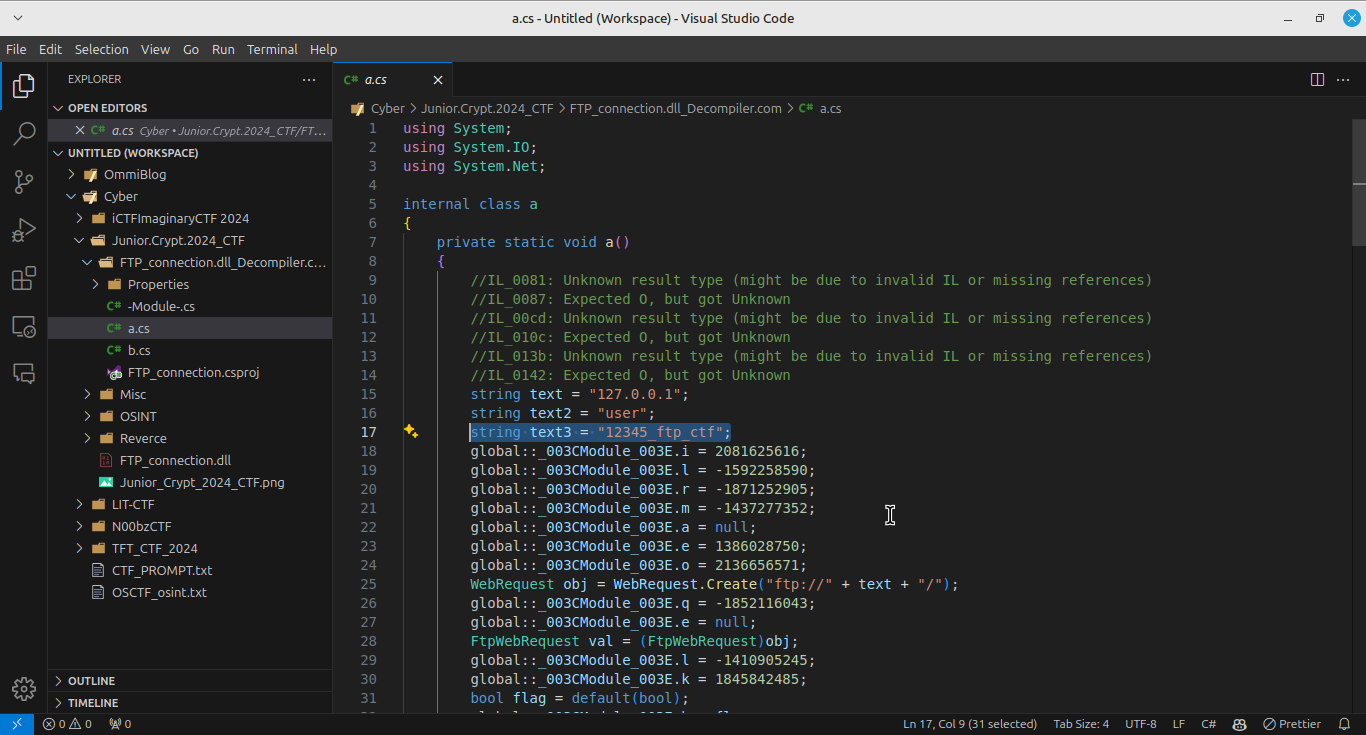
Flag: grodno{12345_ftp_ctf}
Misc
Found on my Windows (50 Points)
Description:
Identify the hash type and retrieve the original password. The flag format is grodno{password}.
Solution:
-
Analyze the Hash:
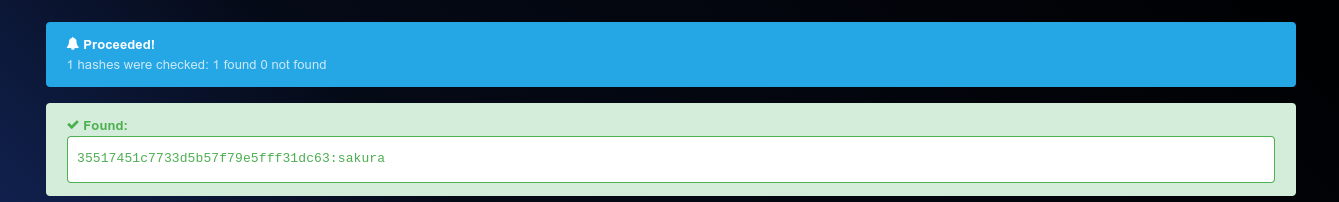
Downloaded the hash filehash1.txtfrom this link.
Hash from File -
Decrypt the Hash:
Used Hashes.com to decrypt the hash, revealing the password"sakura".
Flag: grodno{sakura}
Dogs running in a circle (50 Points)
Description:
Actually, I’m a fan of astronomy. But where would we be today without cybersecurity…
Determine the hash type and get the original string - the password.
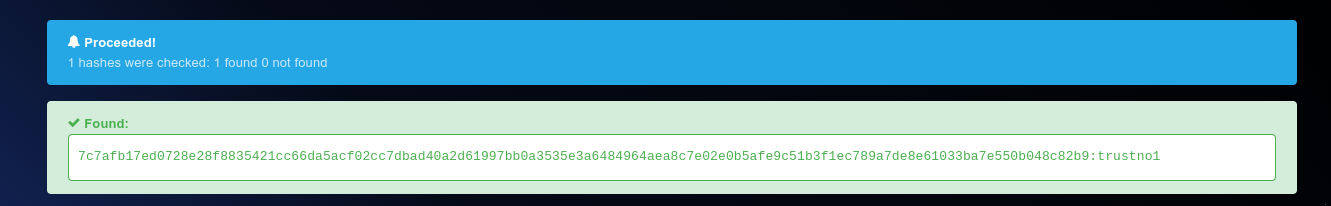
Hash:
7c7afb17ed0728e28f8835421cc66da5 acf02cc7dbad40a2d61997bb0a3535e3 a6484964aea8c7e02e0b5afe9c51b3f1 ec789a7de8e61033ba7e550b048c82b9
Solution:
-
Analyze the Hash:
The provided hash was identified and needed to be decrypted to retrieve the original string. -
Decrypt the Hash:
Decrypted the hash using the same method as the previous which revealed the password"trustno1".
Hash 2
Flag: grodno{trustno1}
My Latest Find (50 Points)
Description:
My latest find. I won’t look for hashes anymore.
Determine the hash type and get the original string - the password.
Hash:
dc31d6b5e25f9fb3e75a40c26b88 9b4b9b76654c110dbda739a9e899
Solution:
-
Analyze the Hash:
Identified the hash type and decrypted it using the same method as previous . -
Decrypt the Hash:
Decrypted the hash to reveal the password"lynlyn123".
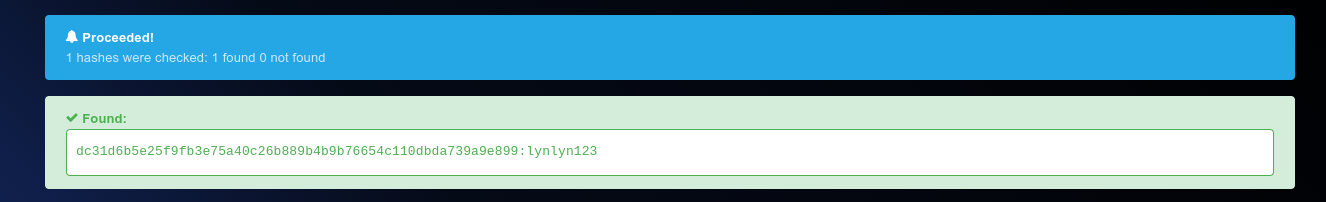
Flag: grodno{lynlyn123}
Reverse
Random Cipher (50 Points)
Description:
You have received an encryption procedure that uses random numbers and text encrypted with it. Restore the original message and find the flag in it.
Files:
Solution:
The Python code provided below decrypts the encrypted message using a random key.
from random import randint
def encrypt(text):
key = randint(1, 2 * len(text))
result = []
for c in text:
result.append(ord(c) + (ord(c) % key))
key += 1
return result
def decrypt(encrypted, initial_key):
result = []
key = initial_key
for value in encrypted:
m = int(value)
for r in range(key):
if (m - r) % (1 + r // key) == 0:
n = (m - r) // (1 + r // key)
if n % key == r:
result.append(chr(n))
break
key += 1
return ''.join(result)
if __name__ == "__main__":
with open("terror.txt", "r") as f:
encrypted_values = f.read().split(" ")
initial_key = 2 * len(encrypted_values)
decrypted_message = decrypt(encrypted_values, initial_key)
print("Decrypted message:", decrypted_message)
Flag: grodno{xa-xa-xa-terrorist}
Mutated Caesar (50 Points)
Description:
The Caesar Cipher has mutated. Now it works not only with English alphabet characters but also with a subset of ASCII characters.
Files:
- Caesare.py (Replace with actual link)
- Caesare_out.txt (Replace with actual link)
Solution:
from hashlib import md5
cipher = '''/:7,67Ct01;'1;'8:7*)*4A'.->-:'.:75'<0-'=88-:'n14-E'''
md5str = '14927c0edb1bfaf21c81d6b88ca9472a'
for n1 in range(0x20, 0x42):
for n2 in range(0x7d, 0x7f):
if n1 >= n2:
continue
CN = {chr(i + n1): i for i in range(0, n2 - n1 + 1)}
NC = {i: chr(i + n1) for i in range(0, n2 - n1 + 1)}
N = len(CN.keys())
for key in range(N):
try:
decrypted = "".join([NC[(CN[c] - key) % N] for c in cipher])
if decrypted.startswith('grodno{') and decrypted.endswith('}'):
if md5(decrypted.encode()).hexdigest() == md5str:
print(f"Found flag: {decrypted} with n1={n1}, n2={n2}, key={key}")
except KeyError:
continue
Flag: grodno{This_is_probably_fever_from_the_upper_Nile}
OSINT
Introduction:
OSINT (Open Source Intelligence) require creative thinking and detailed online research.
Use tools like Google Image Search and Yandex.
Gather clues from articles, forums, and databases.
Capital City (50 Points)

Description: This photo was taken in a historically significant city, which has a rich past and has served as the capital of an important state. The photo includes names and landmarks that help identify the city.
Flag Format: grodno{City_Name;Country_Name}
Example: grodno{Novogrudok;Grand_Duchy_of_Lithuania}
Solution: After careful examination of the photo and historical research, I identified the city as Novogrudok, which was the capital of the Grand Duchy of Lithuania during its early years.
Flag: grodno{Novogrudok;Grand_Duchy_of_Lithuania}
Monument to Cucumber (50 Points)

Description: This monument, dedicated to a cucumber, is located in the town of Shklov in the Mogilev region of Belarus. According to local legend, rubbing the bills in the pocket of the statue brings wealth, and stroking the flower is said to bring a new addition to the family.
Flag Format: grodno{CityName_StatueName}
Example: grodno{Novogrudok_Zubr}
Solution:
The Monument to a cucumber is located in Shklov, a town in the Mogilev region of Belarus. The statue is named “Ogurodets,” which translates to “Cucumber” in Russian. The flag format uses the city name “Shklov,” though it might be rendered as “Shklow” in certain transliterations. After solving it, I realized that the statue’s name is already given in the image file name,ogurodets.jpg
Flag: grodno{Shklow_Ogurodets}
Smugglers (50 Points)

Description:
And take potatoes to the market, and diesel fuel across the border to Poland, and dear to the Belarusian soul… What is this legendary car?
Flag Format:
grodno{Brand_Model_Generation}
Example:
grodno{Volkswagen_Polo_V}
Solution: Based on research and confirmation from this source, the car referred to in the is the Volkswagen Passat B3.
Flag:grodno{Volkswagen_Passat_B3}
Haute Couture (50 Points)

In what year were these models presented at a fashion show in Paris? To create these clothes, famous Valentino designers Maria Grazia Chiuri and Pierpaolo Piccioli drew inspiration from the paintings of the Belarusian artist Marc Chagall.
Flag Format:
grodno{year}
Solution:
After thorough research and verification using Google Image Search, I discovered that the models in the provided image were part of the Valentino Haute Couture 2015 Spring/Summer Women’s Collection, as documented in this Pinterest post.
Flag: grodno{2015}
Architect of Grodno (50 Points)

Description:
In Grodno, on Eliza Ozheshko Street, next to the main building of our university, there is a sculpture of “men on a bench”. This sculpture also has an alternative name - “The Architect of the City Grodno”. But city residents know who exactly is holding the map of old Grodno in their hands. So who do our students see every time they go to university?
Flag Format:
grodno{Nam_Surname}
Example:
grodno{Jean-Claude_Van_Damme}
Solution: Through image search on Yandex, I identified that the person depicted in the sculpture is Giuseppe de Sacco, a notable architect who worked in Grodno.
Flag: grodno{Giuseppe_de_Sacco}
World of Tanks (50 Points)

Description:
On July 29, 2016, the Belarusian airline presented an aircraft in the colors of a popular computer game. Find which airline used this color scheme and name the aircraft model.
Flag Format:
grodno{AirlineName;Airplane_Model}
Example:
grodno{GrodnoLine;Antonov_24}
Solution:
After extensive research, I confirmed that the Belarusian airline Belavia used this color scheme on a Boeing 737-300 aircraft, as seen in this Wikimedia image.
Flag: grodno{Belavia;Boeing_737-300}